Politics
House’s zero trust journey is more process than technology update

The House of Representatives started its journey to push security to the edge by first looking internally.
With hundreds of end points in member offices across the country, House technology leaders had to take stock of what cyber tools they were already using.
Jamie Crotts, the chief information officer for the House of Representatives, said that initial assessment of its current state of cyber tools and how they fit into the zero trust model was the first step in their improving the overall cyber posture of the lower chamber of Congress.
Jamie Crotts is the chief information officer for the House of Representatives.
“We plan on a three-year technology roadmap cycle. So it’s about understanding which step is the next best step to get us the most benefit for the architecture and for our users. And from that point, we adjusted our roadmap and our planning,” Crotts said on Ask the CIO. “We began budgeting for some of the larger items that are going to be more long term, and we began implementing things that we could do immediately, that were more quick wins, if you will, and that’s still where we are.”
While the House doesn’t have to meet the executive branch mandates under zero trust, Crotts said the maturity models developed by the Cybersecurity and Infrastructure Security Agency and Defense Department are helping to guide their efforts.
The initial zero trust assessment mapped against their current IT roadmap, which is broader than just cybersecurity, led to some adjustments for current and future planning as well as where to invest its limited budget.
Crotts said that mapping led the team to realize that achieving initial capabilities under zero trust was as much as about adjusting the way they did cybersecurity as it was about new tools.
“Looking at it from the users, devices, applications and the network, every single layer of that, we examined how our efforts were going to be able to make improvements. When we looked at the assessment and we saw we can get better at, say, provisioning of devices for users, we can do things a little bit differently that will get a slightly more secure device in their hands in a slightly faster time frame. That is something that would be low hanging fruit for us,” he said. “If it’s as simple as adjusting the way we do imaging to make sure it’s inclusive of certain types of tools, we would be able to take care of that without having to plan for a long-term investment that wasn’t already there. We’re not buying a new tool. We’re adjusting an existing process, and that’s most of our quick wins.”
Flexibility remains key to meeting cyber needs
At the same time, Crotts said they are optimizing existing cyber tools to push them closer key areas of zero trust.
“We spend a lot of money on these tools, whether they be cyber tools, specifically, monitoring analysis tools or general IT productivity tools, applications and suites. But we rarely take the time after we have purchased and implemented it to step back and say, ‘Are there other toggles we could adjust that give us a bit more benefit?’ So, part of our assessment from the zero trust side did exactly that,” he said. “It pointed out that we have some investments in tools giving us a bit of an overlap, which can result in a cost savings. If we identify turning on this widget and this tool actually allows us to stop buying this other tool, that’s a win. That’s essentially how we spent the last year, looking at the tools that we’ve already invested in reducing technical debt is something everybody’s trying to do. So every quick win we can get is amazing.”
Like most IT organizations, the House budgets on a multi-year cycle, so Crotts said they do their best to guess what cyber tools or IT applications they will need in a few years. He said having flexibility in existing tools and processes helps close gaps that otherwise they would have to wait for funding to address.
One example is how the House implemented cloud access security broker (CASB) capabilities.
“It might not be doing exactly what we want it to be doing, or we want to look at the way we do our web access firewalls a little bit differently or routing traffic differently coming from the far edge, things like that take a little bit more time,” he said. “We have to do that thorough analysis. We have to make an investment once we pick the right tool that’s going to work for our architecture. That’s really how we chalked up all of those things, so not necessarily by the pillar that they naturally belong in, but across all the pillars, where can we actually have the most innovative benefit for the House?”
With some initial zero trust capabilities implemented, Crotts said the next focus area is around the data pillar.
Focusing on the data pillar of zero trust
He said his team is spending a lot of time understanding their data governance model.
“Data is data, but the importance of that data is unique to the organization that creates it. Nowhere is that more true than in the legislative branch, where we have different types of data that other people don’t have to deal with, things like legislation data that’s protected by the Speech and Debate Clause of the Constitution. Those types of non-traditional data governance problems, if you will, are things that we’re trying to wrap our minds around,” Crotts said. “How do you do proper tagging of that kind of data? How do you understand the flow of that data throughout your enterprise? When it’s not as simple as tagging a Social Security Number automatically because I know what that looks like, but for some of these more ethereal concepts, it takes a real understanding.”
Crotts added that means analyzing current and possibly future tools to help manage the data as well as creating schemas that let data move securely and efficiently through the network.
“A lot of good security practices come back to the fundamentals of, can you invoke it in a policy and actually enforce it? So once we understand the data types in the data flow, and we get sort of the organizational agreement on, ‘Yes, these are the things and this is the level at which we want to want and need to protect them,’” he said. “Then setting up that structure becomes the next challenge, if you will. A lot of best security practices can be put in play there, but like everything else, you need to define it first.”
Once the House can define and manage its data, then applying a more strict version of privileged access management to further protect systems and data will be possible.
At the same time, Crotts said his team has to understand their users’ needs, of which there are thousands of people on Capitol Hill and across 900 district offices that need access to systems and data, to balance their experience with the cybersecurity requirements.
“A proper security tool configured well does not have to interrupt workflow. And that’s really key to understanding those challenges,” he said. “Every time a user has to stop and log into something else or authenticate or pull up their token numbers and reauthenticate, you have lost them. They become upset with the process, even if it’s perfectly efficient, you’ve interrupted them. You should only do that as little as possible. But then you need to trust that once they are logged into that session, that you’ve got the other controls in place to make sure that the accesses prevent them from moving laterally to a place where they shouldn’t be. If you’ve got all that in place, then you can trust that login and you don’t have to go through all those other processes.”
The post House’s zero trust journey is more process than technology update first appeared on Federal News Network.
Politics
Mainstream Media in Disbelief as Trump DOUBLES Expected Jobs Numbers – President Trump Takes Victory Lap After Adding 130,000 Jobs to US Economy


US jobs numbers for February far exceeded expectations to start 2026.
President Trump doubled expectations adding 130,000 jobs when only 55,000 was expected.
The unemployment rate also decreased from 4.4% to 4.3% according to CNBC
President Trump: Just in: GREAT JOBS NUMBERS, FAR GREATER THAN EXPECTED! The United States of America should be paying MUCH LESS on its Borrowings (BONDS!). We are again the strongest Country in the World, and should therefore be paying the LOWEST INTEREST RATE, by far. This would be an INTEREST COST SAVINGS OF AT LEAST ONE TRILLION DOLLARS PER YEAR – BALANCED BUDGET, PLUS. WOW! The Golden Age of America is upon us!!! President DJT
From the president’s Truth Social account:
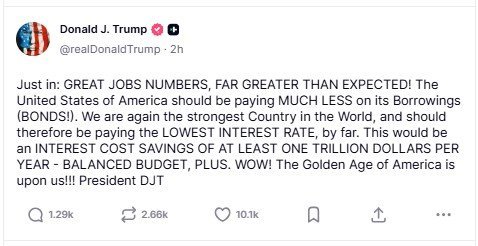
At what point can the American people sue the Federal Reserve Chief for his dereliction of duty? Jerome Powell is now costing every American untold amounts of money by refusing to do his job!
CNBC host Rick Santelli reacted positively:
BREAKING: CNBC is in a STATE OF SHOCK after President Trump DOUBLES expected jobs numbers
“Coming in TWICE EXPECTATIONS at 130,000. 130K!”
Trump and Scott Bessent VINDICATED!
pic.twitter.com/08hdz9udob
— Eric Daugherty (@EricLDaugh) February 11, 2026
Even CNN was forced to share the good economic news.
Wow, even CNN says that the jobs report is good for the economy!
“This is a hot jobs report. I mean, there’s really nothing in this not to like. You’re seeing a lot of sectors that had been softer like manufacturing, for example, looking better. You’re seeing numbers that really… pic.twitter.com/rfZ9JA5mRr
— DeVory Darkins (@devorydarkins) February 11, 2026
The post Mainstream Media in Disbelief as Trump DOUBLES Expected Jobs Numbers – President Trump Takes Victory Lap After Adding 130,000 Jobs to US Economy appeared first on The Gateway Pundit.
Politics
Democrat Rep. Nadler Has to be Woken Up by Staffer During Bondi Hearing (VIDEO)


Democrat Rep. Jerrold Nadler (NY) had to be woken up by a staffer on Wednesday morning during a congressional hearing.
US Attorney General Pam Bondi testified at a House Judiciary Committee hearing on the Epstein files, fatal shootings of two anti-ICE agitators and more.
Nadler fell asleep just minutes into Wednesday’s hearing.
A staffer walked over to Nadler and woke him up.
WATCH:
Later on during the hearing, Nadler and Bondi got into a shouting match over Jeffrey Epstein’s co-conspirators.
“How many [co-conspirators] have you indicted?” Nadler asked Bondi.
“Excuse me! I’m going to answer!” Bondi said.
“Answer my question!” Nadler demanded.
“I’m gonna answer the question the way I want to answer the question. Your theatrics are ridiculous,” Bondi said.
“Chairman Jordan, I’m not gonna get into the gutter with these people,” Bondi said.
Bondi and Nadler continued to talk over each other until Chairman Jim Jordan intervened.
WATCH:
NOW – Pam Bondi, when asked how many of Epstein's co-conspirators she's indicted or is actively investigating: "I'm going to answer the question the way I want to answer the question. Your theatrics are ridiculous." pic.twitter.com/9EyDNK7val
— Disclose.tv (@disclosetv) February 11, 2026
The post Democrat Rep. Nadler Has to be Woken Up by Staffer During Bondi Hearing (VIDEO) appeared first on The Gateway Pundit.
Politics
Possible Trans Attack?- ‘Gunperson’ Wearing Dress Kills 9 and Injuries at Least 25 Others at Canadian School

Creative Commons Attribution-Share Alike 3.0 Unported license./ Author: Dickelbers
According to the Tumbler Ridge Royal Canadian Mounted Police (RCMP), a mass shooting at Tumbler Ridge Secondary School in British Columbia left nine dead and at least 25 more injured.
According to police, the sole suspect, described as a “gunperson’ wearing a dress, was found dead inside the school from “a self-inflicted injury.”
Per CNN:
Police found six people dead and dozens injured when they arrived at the high school in Tumbler Ridge, a town of just 2,400 people in northeast British Columbia, early on Tuesday afternoon. Another person died en route to hospital, police said.
The alleged shooter, who was found dead at the school with a self-inflicted injury, is believed to have killed two more people, whose bodies were discovered at a home in the township
Two victims were airlifted from the school to hospital with serious or life-threatening injuries. And about 25 other people were also being treated at a local medical center, police said.
BREAKING: 10 people are dead, 25 injured after a “woman wearing a dress” opened fire on a school in British Columbia, Canada
Local police are referring to the shooter as a “gunperson.”
Yeah, we all know this is yet another trans mass shooter. pic.twitter.com/McA9C0nmcc
— Nick Sortor (@nicksortor) February 11, 2026
Fox News reported that Superintendent Ken Floyd, North District Commander, said in a statement, “This was a rapidly evolving and dynamic situation, and the swift cooperation from the school, first responders, and the community played a critical role in our response.”
“Our thoughts are with the families, loved ones, and all those impacted by this tragic incident. This has been an incredibly difficult and emotional day for our community, and we are grateful for the cooperation shown as officers continue their work to advance the investigation.”
Juno News, an independent outlet in Canada, claims to have spoken with someone connected to the suspected shooter’s family who says the suspect was trans and used “she/her” pronouns, but authorities have not confirmed the claim.
The Guardian reported that the police have identified the shooter, but didn’t publicly release their identity due to the integrity of the investigation.
The shooter’s identity, any potential connections to groups, and motivations remain under investigation.
The post Possible Trans Attack?- ‘Gunperson’ Wearing Dress Kills 9 and Injuries at Least 25 Others at Canadian School appeared first on The Gateway Pundit.
-

 Tech2 weeks ago
Tech2 weeks agoSend Help review: GLOP! Youre not ready for Rachel McAdams latest… but I love it
-
Business5 months ago
How I Paid Off My Mortgage 10 Years Early On A Teacher’s Salary
-

 Politics5 months ago
Politics5 months agoBlack Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle
-
 Tech5 months ago
Tech5 months agoGet a lifetime subscription to the “ChatGPT for investors” for under $60
-

 Tech5 months ago
Tech5 months agoReview: The Dreame H15 Pro CarpetFlex is the first wet/dry vacuum I liked
-
Business5 months ago
25 Low-Effort Side Hustles You Can Start This Weekend
-
Business5 months ago
9 Ways to Command a Six-Figure Salary Without a Bachelor’s
-

 Entertainment4 months ago
Entertainment4 months agoFat Joe Recalls Bruno Mars Snapping on Him Over Question About Puerto Rican Roots: ‘Broke My Heart’




